
The latest security flaw in iOS

A now-patched iOS vulnerability could let malicious apps silently steal your iCloud data with no alerts, and no consent.
The team at Jamf Threat Labs has discovered a big security issue in Apple’s Transparency, Consent, and Control (TCC) system. The flaw, tagged as CVE-2024-44131, can let apps access your private stuff like photos and location details without you even knowing.
Apple has already fixed the vulnerability in iOS 18 and macOS 15, but it’s a wake-up call about mobile security and keeping our data private. The TCC system is supposed to alert you when apps want to access your private data, like your photos or location.
But this vulnerability takes advantage of weaknesses in Apple’s FileProvider and fileproviderd processes, letting bad apps slip past the checks. Once they exploit this, they can grab your data without raising any alarms or asking for permission.
Unauthorized access to iCloud
Both macOS and iOS systems are affected, showing that bad actors are now targeting vulnerabilities across different platforms, especially when it comes to services like iCloud. Such vulnerabilities challenge the belief that mobile devices are safer than desktops.
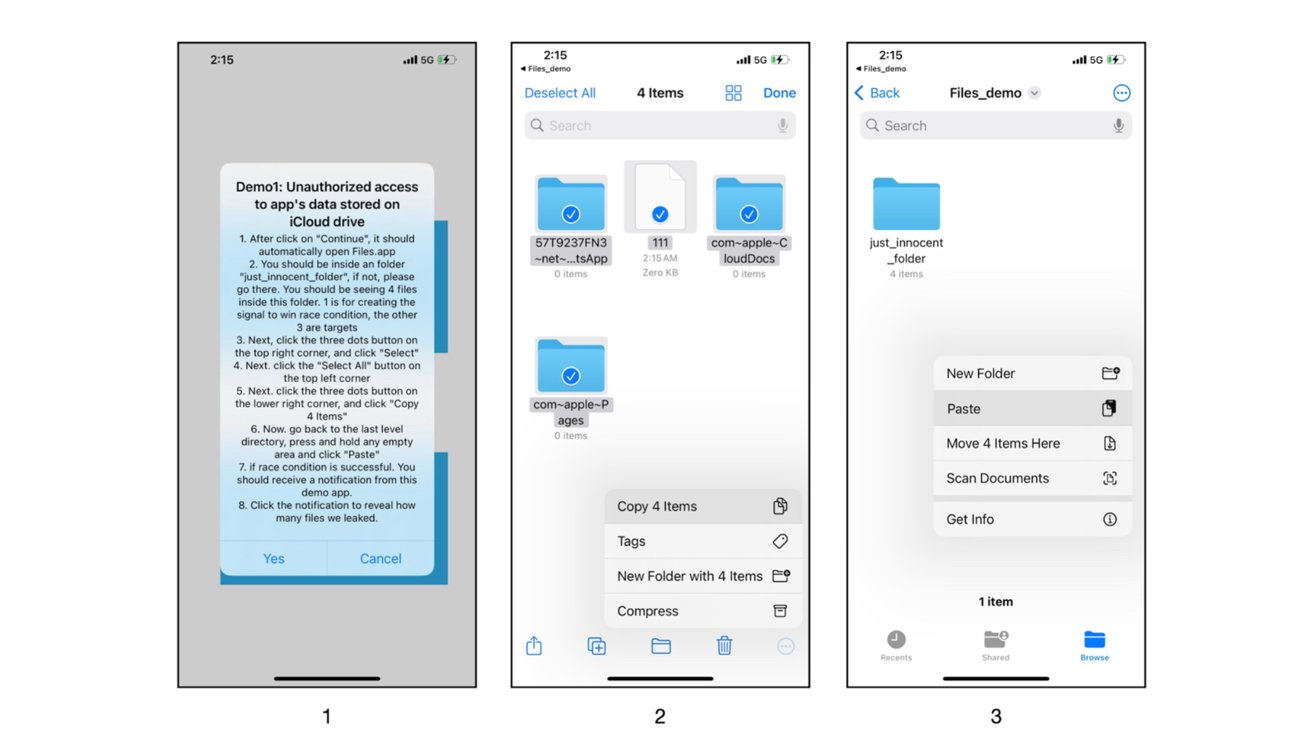
A malicious app demo. Image credit: Jamf Labs
The exploit messes with symlink race conditions in Apple’s Files.app and fileproviderd processes.
- Symlink Trickery: A shady app hijacks file operations by Files.app, rerouting them to directories it controls using perfectly timed symlinks.
- Taking Advantage of Privileges: By abusing the fileproviderd’s elevated privileges, the rogue app can grab sensitive user data without triggering any TCC alerts.
For example, Apple’s defenses can detect symlinks at the end of file paths, but this trick drops symlinks in the middle, sneaking past detection.
The exploit targets specific directory paths that Files.app and fileproviderd can access. Here’s what they’re after:
- iCloud Data: Paths like /var/mobile/Library/Mobile Documents/ could be hit, including backups for apps like WhatsApp, Apple’s Pages, and other iCloud-synced files.
- Common UUID Directories: While many apps use unique UUIDs for security, some shared directories (like /Mobile Documents/com~apple~CloudDocs/) are consistent across devices, making them easier to exploit.
How to stay protected
Apple fixed the vulnerability in iOS 18 and macOS 15 after Jamf alerted the company. It’s good news, but it shows that no platform is safe from getting hacked.
First, make sure all your devices are running the latest iOS and macOS versions so you’ll have the latest security patches. Businesses and users need to treat mobile devices like they’re high-risk endpoints. Strengthening mobile security is no longer optional.
To keep your iPhone safe, keep an eye on who can access it and watch for any strange file activity. This extra layer of protection can help you spot any attempts to break in and prevent any data breaches.




