
macOS Gatekeeper is used to validate macOS apps.

In previous versions of macOS Gatekeeper, Control-click could be used as a launch override for running downloaded apps. Apple has now changed that.
Under earlier versions of macOS, users could override Apple’s Gatekeeper security to launch apps in the Finder by Control-clicking on them to launch them.
The override was only needed on an app’s first run, but it’s still annoying nonetheless to some users.
What is Gatekeeper?
Apple added Gatekeeper and the Mac App Sandbox to macOS years back as a way to try to thwart malware. It ensures any app you download from the Mac App Store is authentic and has also been verified by Apple.
Around the same time, Apple also added Developer ID to certify non-App Store apps from registered Apple developers. It also brought in Notarization, in which developers can submit their apps to Apple for approval.
These four parts, along with System Integrity Protection (SIP), help keep Mac apps and files more secure at runtime.
You can set Gatekeeper and Developer ID settings in System Settings->Privacy & Security->Security by choosing whether to allow only App Store apps (Gatekeeper), or both Gatekeeper and Developer ID apps.
The Finder will respond differently to each app launch based on these settings.
It’s also possible to bypass some of these security features by turning off SIP in the Terminal – but Apple doesn’t recommend it.
Control-click override
Before macOS Sequoia, users could override the Gatekeeper warning in Finder by Control-clicking on an app when launching it. In Sequoia, Apple has now removed this bypass in another effort to secure or lockdown the Mac.
If you get a warning that an app is from an unknown developer, or that it needs to be moved to the Trash, first go to System Settings->Privacy & Security->Security and check for the Open Anyway button. You’ll be prompted for an admin password to run the app.
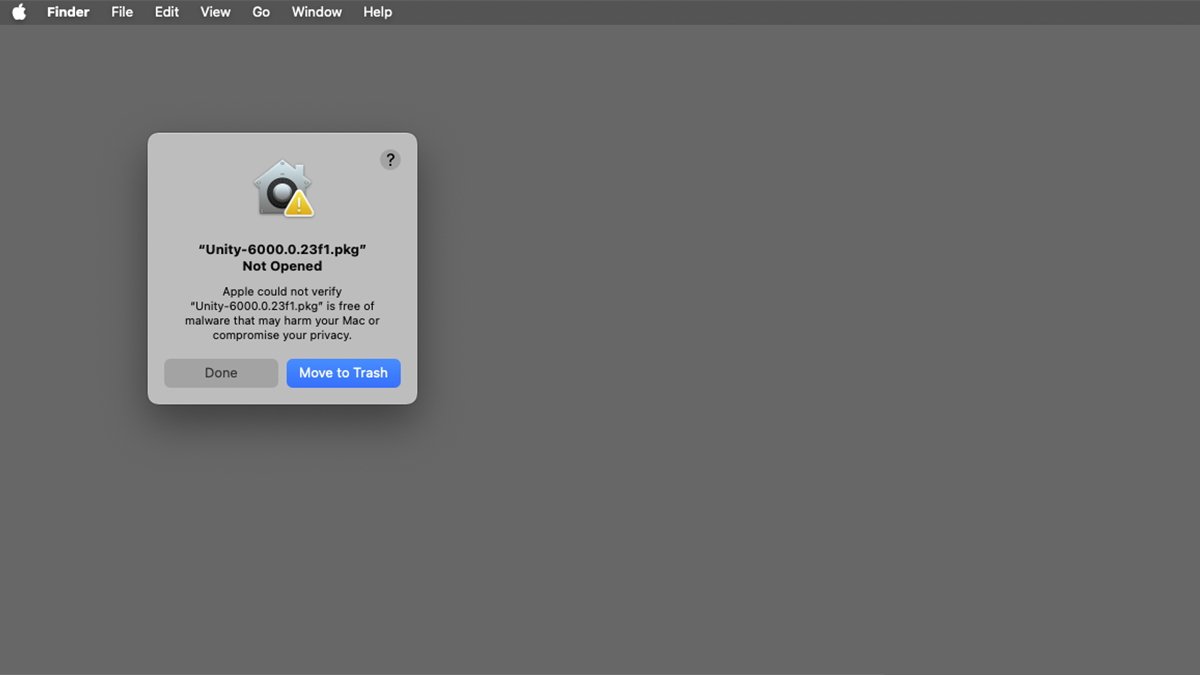
A downloaded installer app which is outside of Gatekeeper verification.
As Michael Tsai noted on his blog, there’s also still an annoying bug in Gatekeeper in Sequoia which may erroneously report an app as damaged, even when it’s not, if the app has been notarized by Apple.
Apple removing the bypass may cause more annoyance for some Mac users, since doing so now requires a trip to System Settings on every app first run for non-Mac App Store apps. There’s not much users can do about this other than disabling SIP, which again, Apple doesn’t recommend.
Also, note that as this article mentions, third-party Mac developers have to add an extended attribute to their app download distributions (com.apple.quarantine) if the apps are distributed outside the Mac App Store. Although most developers will honor this requirement, it’s still possible that some won’t – leaving some downloads as a security risk which can bypass some of Apple’s app security in some cases.




